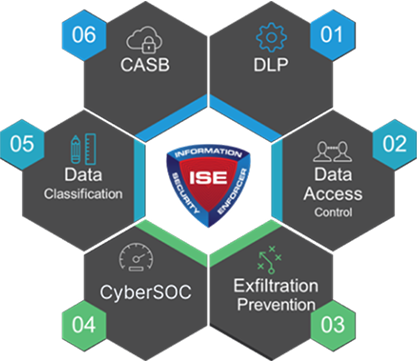
In a world of exponential data growth and sprawl, our ISE™ AI-powered, 4th Generation Cybersecurity platform is the Gold Standard in protecting and controlling enterprise data, content and information.

GC CyberSecurity’s ISE™ is the first and only 4th Generation Cybersecurity platform that provides complete control over securing information and data assets from accidental disclosure or malicious theft and exfiltration attacks.
Auto-Classify data and information in real-time, at any level of granularity
Auto-synthesize the rules, roles and identity of actors and their access authorization to data & information
Auto-enforce data governance policies using military-grade Segmentation of Duty (SOD)
Monitor and control enterprise systems and clouds with a centralized command and control center
Malicious insiders exploit their legitimate access to exfiltrate sensitive data via email channels, bypassing traditional security controls and causing significant financial, reputational, and compliance damage
Automated and advanced e-mail data protection systems employ Deep-AI, behavioral analytics, and information classification to detect suspicious patterns, unauthorized transfers, and policy violations in real-time before sensitive data leaves the enterprise
Enterprises gain continuous protection against insider threats with minimal false positives, maintain regulatory compliance, protect intellectual property, prevent data breaches, and reduce security team workload through accurate automated detection that stops data loss while allowing legitimate business email communications to continue unimpeded
Sophisticated malware and ransomware attacks can infiltrate enterprises' networks, encrypt critical data, exfiltrate sensitive information to threat actors, and cause devastating operational disruptions, financial losses, and compliance violations
Automated advanced data protection systems employ advanced threat detection, behavioral analysis, anomaly identification, and zero-trust, actor-centric architectures to continuously monitor for malicious activities, isolate suspicious processes, prevent unauthorized data movements, and maintain immutable backups of critical information
Enterprises achieve dramatically improved resilience against evolving cyber threats, significantly reduced attack surface, minimized data breach impact, faster incident response times, continuous regulatory compliance, and preserved business continuity without overwhelming security teams or disrupting legitimate business operations
Enterprises struggle to identify and protect massive volumes of diverse sensitive data moving across networks, applications, and user devices, leaving critical information vulnerable to breaches and compliance violations. Simple manual Keyword and Lexical Matches are error prone resulting in high False Positives and are highly susceptible to Malicious Data Leak scenarios
Automated classification systems leverage DEEP-AI, and domain-aware pattern recognition to accurately identify, categorize, and tag sensitive structured and unstructured data-in-motion, in any format, in real-time without human intervention, enabling immediate policy enforcement before information reaches unauthorized destinations
Enterprises achieve comprehensive visibility into data flows, maintain continuous regulatory compliance, reduce security team burden, prevent costly data breaches, enable granular access controls, and support informed business decisions through precise risk awareness without impacting legitimate data transfers or user productivity
Enterprises face significant risks when employees accidentally or maliciously transfer large sensitive files through unauthorized channels, bypassing security controls and potentially causing data breaches, compliance violations, and intellectual property loss
Automated file transfer protection systems continuously monitor network traffic, file repositories, and communication channels to detect unusual file movements, classify sensitive data in real-time, and enforce granular policies that block unauthorized transfers while allowing legitimate business operations
Enterprises gain comprehensive protection against data loss without burdening security teams, maintain regulatory compliance, preserve intellectual property, prevent costly breaches, reduce incident response time, and maintain business productivity by stopping only truly risky transfers while allowing approved workflows to continue unimpeded
Modern enterprises struggle with fragmented security systems that generate overwhelming alerts without domain context, leading to detection gaps, delayed remediation of data security incidents, and increased risk of breaches despite significant security investments
Automated cyberSOC-powered platforms integrate Deep-AI-driven analytics, comprehensive visibility across environments, and orchestrated response capabilities to detect sensitive data violations in real-time, prioritize actual threats, and automatically implement remediation actions based on security policies
Enterprises achieve dramatically faster threat detection and response times, reduced security team burnout, continuous compliance with evolving regulations, minimized data breach impacts, improved security ROI, and comprehensive protection across hybrid environments while maintaining business operations through intelligent, context-aware automated remediation workflows